12 Mobile App Security Best Practices Every Developer Should Know

Mobile App Development
Whenever it comes to mobile app development, mobile app security remains the number one concern for all developers as a single breach not only can tarnish the business’s reputation but also may end up wasting all their development efforts. In today’s world full of hackers, where mobile app security threats like Data Leakage, Network Spoofing, and Spyware are a very common thing, mobile app security is not a matter of ‘whether we need it or not’, but essentially is a matter of ‘how strong it could be’.
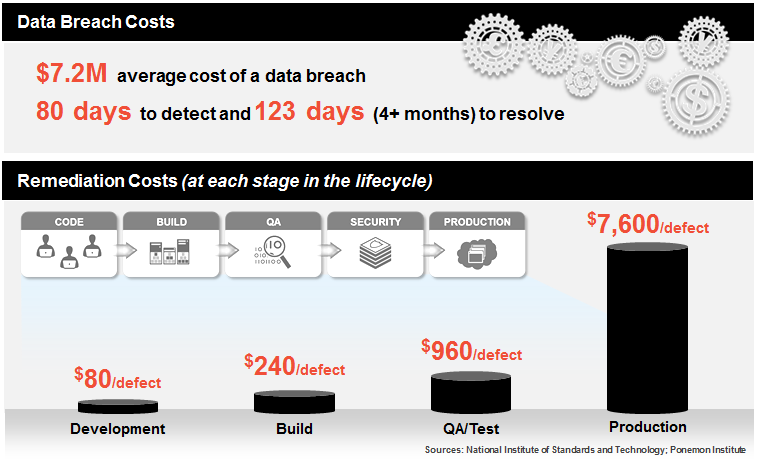
Nonetheless, despite a number of mobile app testing tools available in the market today, the biggest irony is that 85% of app store apps violate mobile app security standards. Since mobile app security is one of the key factors that determine the success or failure of an application, you should make every effort to tighten the security of your mobile apps. To help you out, here are some best practices that you can follow to improve your mobile app security.
Let’s dive into them one by one!
Think Security Early On
No matter how excited you’re about getting your app live, mobile app security must be a key part of your mobile app development strategy from the very beginning. Having a well-planned mobile app security checklist in place will not only help you inculcate all mobile app security measures necessary to make the app fully secure beforehand but also will save you from costly, time-consuming fixes later.
Write a Secure, Hack-proof Code
This is where it all begins! Since Code is the most vulnerable part of any mobile application, you must pay special attention to make your application code as secure as possible. For instance, to harden your code against most common mobile app security attacks, you can take advantage of mobile app security techniques like OWASP methodology, Minification, Obfuscation, Content Controls, and, ‘Open in’ Restrictions.
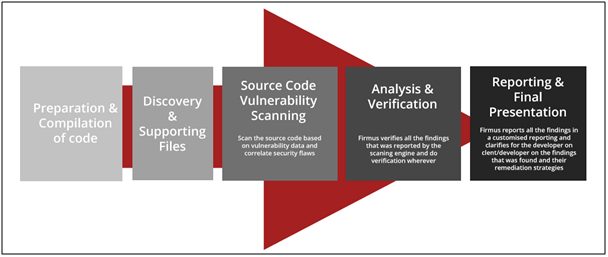
Image Source: Firmus
Encrypt All the Data
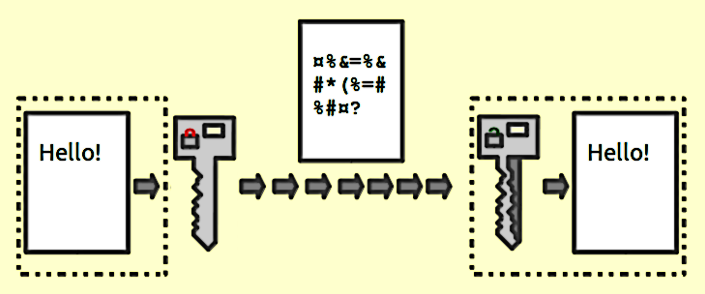
Mobile app security is not limited to just securing the source code. It also requires securing the data that is being stored on the mobile device or transmitted between the application and the back-end server. As Encryption is the one and only way to make it impossible for hackers to read your application data, try to develop your app in such a way that every single unit of data included in the app is encrypted very well. This is one of the key mobile app security best practices.
Be Careful While Using Third-party Libraries
Third-party libraries are quite prevalent among developers for the code building. While these libraries speed up the development of a mobile app to a great extent, they can sometimes make your app vulnerable to hackers as most of them contain malicious code which is often injected by their creators. Since you can never compromise with your mobile app security, always use tried-and-tested third-party components and libraries to avoid any mobile app security loopholes.
Use Only the Authorized APIs
If not implemented authentically, APIs used to integrate third-party libraries and services can also prove to be a curse for your mobile app security. According to a recent survey, APIs is a new and fastest-growing cybersecurity risk, providing hackers with multiple avenues to access a mobile application’s data. Hence, experts recommend using a centralized authorization to ensure the maximum mobile app security.
Implement High-Level User Authentication
Authentication and authorization are two of the key components of mobile app security. While a large part of these two factors depends on the end users of your mobile application, it’s your responsibility as a developer to encourage the users to be more conscious about authentication and authorization. Even if your app doesn’t deal with highly-sensitive information, you should always take advantage of cutting-edge mobile app security technologies such as OAuth 2.0, JSON web tokens and OpenID Connect protocol to make your app more secure.

Understand Platform-specific Limitations
If you’re developing an app for multiple mobile operating systems, you should keep in mind that every platform has its own specific limitations that can affect the security of your mobile app. Given the fact that most of the Android and iOS devices get hacked through either the operating system or hardware vulnerabilities, you need to first understand platform-specific mobile app security limitations and then code accordingly.
Deploy Tamper Detection Techniques
Tamper detection techniques are used to get alerts whenever someone tries to tamper with your code or inject malicious code to your application’s source code. As a developer, you can include various tamper detection and anti-tamper techniques, such as app signature verification at runtime, app installer identification, activity logs, and performing environment checks, to get warned about such mobile app security flaws.
Leverage The Principle of Least Privilege (POLP)
While we’re discussing the mobile app security, how we can overlook the principle of least privilege that dictates a code should run with only those permissions that are absolutely essential for its functioning and nothing more than that. As a developer’s perspective, you should never request any more privileges than the minimum required for your mobile app to function. Remember, the less your app knows, the better!
Implement Proper Session Handling
Given the fact that sessions on mobile devices usually last much longer than the ones on desktop devices, proper session management becomes a crucial aspect of mobile app security. Particularly in case of stolen and lost devices, you must provide users the facility to remotely log-off their account and wipe off all data presented on their devices. To further increase your mobile app security, you can use tokens instead of device identifiers to validate a session.
Use the Best & Latest Cryptography Tools and Techniques
When it comes to encryption of your mobile application’s data, the most important mobile app security practice you should follow is the Proper Key Management. As a preventive mobile app security measure, you should neither hard code your encryption keys nor store your keys on local devices. Also, instead of cryptographic protocols like MD5 and SHA1, always use state-of-the-art encryption protocols such as 256-bit AES and SHA-256 for hashing.
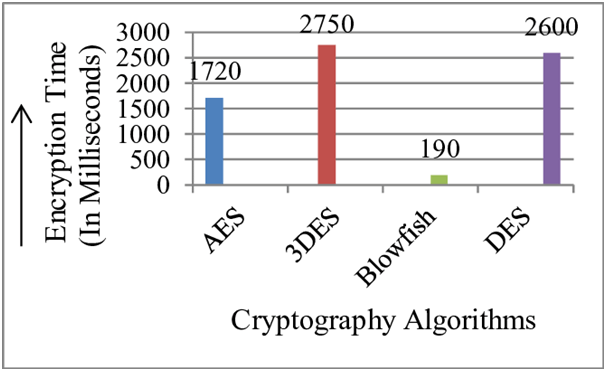
Image Source: Toolbox.com
Test & Update Regularly
Securing your mobile app is not a one-off task. It is indeed a never-ending process that you need to perform on a regular basis. Surprisingly, but true nonetheless, improper and irregular testing is one among the several reasons responsible for the failure of a mobile app. Hence, test your mobile app regularly and fix any loopholes or vulnerabilities you find with each new update and version released.

Hopefully, you’d find this article informative and valuable. If you’re looking for developers to build a well-functioning, secure mobile app, feel free to contact us.